Single Sign On Specification
Purpose
This document is intended for Recordkeepers (synonymously referred to as clients) and outlines the technical implementation and specifications for signing on to the Morningstar® Retirement ManagerSM application and receiving real-time transactions back from Morningstar® Retirement ManagerSM.
Definitions
SSO:
Single sign-on (SSO) login process by which Recordkeepers will link directly to the Morningstar® Retirement ManagerSM web application on behalf of participants.
Contents
- SSO Overview
- SAML 2.0 SSO (Morningstar Standard Implementation)
- SAML HTTP Request to Morningstar
- SAML signing
- SAML encryption
- SAML Assertion Authentication and Validation
- SAML Attributes
- Login and Data Errors
- SAML FAQ
SSO Overview
Login and data retrieval can be accomplished via three different methods of SSO:
- SAML 2.0 (Preferred and currently supported) and SAML 1.0 (still supported)
- Web Services (Legacy)
- HTTPS Post (Legacy)
SAML 2.0 SSO (Morningstar Standard Implementation)
SAML 2.0 (IdP initiated browser POST profile) is the standard SSO process for Morningstar® Retirement ManagerSM implementations. The participant first logs into the client website (Identity Provider). After logging into the client website, when a participant chooses the option to navigate to Morningstar® Retirement ManagerSM, they will be signed on to the Morningstar® Retirement ManagerSM (Service Provider) without needing to log in again. This will be done using SAML 2.0.
SAML HTTP Request to Morningstar
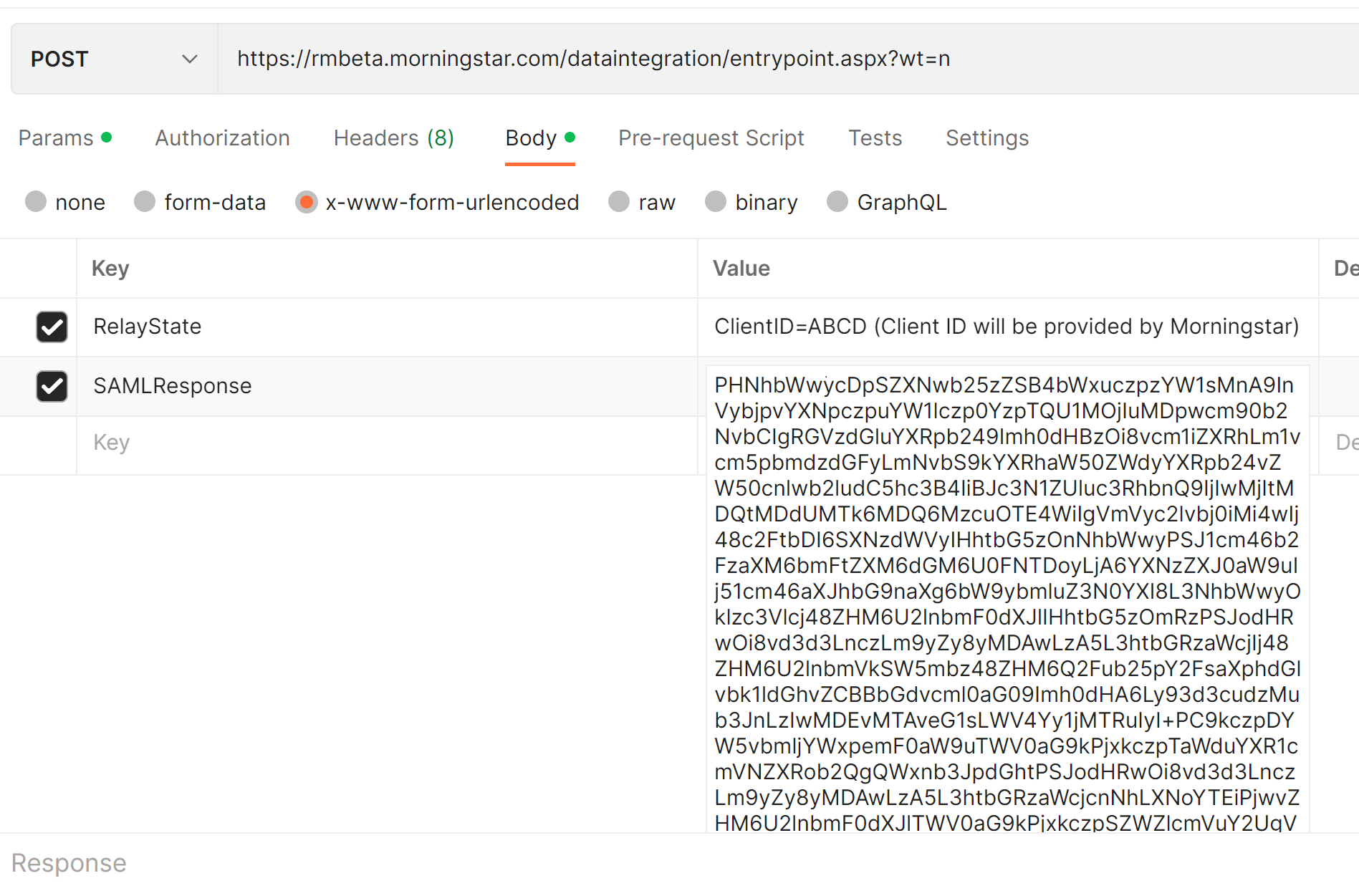
The SAML assertion should be sent as an x-www-form-urlencoded HTTP Post request with two parameters:
| Name | Value |
|---|---|
| Relaystate | ClientID=”MorningstarAsssignedClientID” |
| SAMLResponse | base64 encoded SAML assertion |
| The following image shows an example of the SAML post request to Morningstar lower environment: |
SAML Signing
The SAML assertion must be signed by the client using their private key. The client should share the public key/certificate counterpart of this private key during the development phase. This certificate is installed on Morningstar’s servers and used to validate the SAML assertion. The client can choose to use different certificates/public key for Production and lower environments. To avoid SSO failures, a few months before the certificate expires, the client must send an updated certificate to Morningstar via email.
In the SAML, the following signature algorithms and methods are supported:
CanonicalizationMethod
- xml-exc-c14n
SignatureMethod
- rsa-sha1
- rsa-sha256
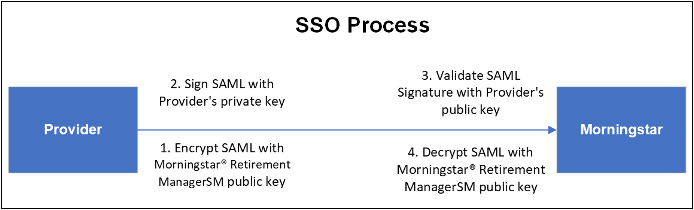
SAML Encryption
Morningstar supports encrypted SAML assertions. However, we do not mandate encrypting the SAML assertion. It is an optional step that the client may choose to perform. We support:
- Encrypting specific SAML attributes
- Encrypting the entire SAML assertion
To support encryption, Morningstar will send our public encryption key to the client during the development phase. The public encryption key is different for the Production and lower environments. The client is expected to encrypt the SAML using the key provided by us. Our certificates typically expire in one to two years. Morningstar will initiate communication with the client on a timely basis and provide updated certificates.
The signing and encryption flow is shown below:
SAML Assertion Authentication and Validation
Morningstar will validate the SAML assertion sent by the client in accordance with SAML 2.0 specifications. Morningstar will validate that they are the intended party for the assertion and that the assertion is compliant. Some of the things that Morningstar will check are the following (not an exhaustive list):
- The SAML signature of the assertion to ensure that the correct party has signed it and the payload has not been tampered in transit
- If assertion is encrypted, the encryption certificate and signature
- The values of Recipient, Audience, and Destination nodes in the assertion
- The Issuer value (Issuer value will be shared with the client in advance during development phase)
- The timestamps in the Conditions node values to confirm that they are the intended party for the Assertion and will also validate the Issuer value to confirm that the Assertion was generated by client
SAML Attributes
Required:
- Payload
The payload attributes should contain the participant information in plain XML format, conforming to the RTParticipantInput.xsd XML schema shared with the client. Expand the following examples to view the participant XML included in a SAML assertion.
Example 1: SAML XML:
<samlp:Response Destination="https://rmbeta.morningstar.com/dataintegration/entrypoint.aspx" ID="_5c5dacfa-a3fe-48ab-887a-4c94d5d18491" IssueInstant="2021-06-15T07:21:38.991Z" Version="2.0"
xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol">
<saml:Issuer xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion">IssuerID</saml:Issuer>
<Signature xmlns="http://www.w3.org/2000/09/xmldsig#">
<SignedInfo>
<CanonicalizationMethod Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#"/>
<SignatureMethod Algorithm="http://www.w3.org/2000/09/xmldsig#rsa-sha1"/>
<Reference URI="#_5c5dacfa-a3fe-48ab-887a-4c94d5d18491">
<Transforms>
<Transform Algorithm="http://www.w3.org/2000/09/xmldsig#enveloped-signature"/>
<Transform Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#">
<InclusiveNamespaces PrefixList="#default samlp saml ds xs xsi"
xmlns="http://www.w3.org/2001/10/xml-exc-c14n#"/>
</Transform>
</Transforms>
<DigestMethod Algorithm="http://www.w3.org/2000/09/xmldsig#sha1"/>
<DigestValue>iLIX82EKOnxIWVOt7ZvP+EFPNX8=</DigestValue>
</Reference>
</SignedInfo>
<SignatureValue>j3zjQRT+HIZ9pIq3mHkr8U93M0saqSIwIxOHLV/NkBMImmADxuk1mU6yZIxzbrEL2zltPujVHI2OWkqoseVmxg1WO13saZj7zXI/Og/UPJEY2ZeOrUwxug9C+n1nkjuRyfv2nNnmcD9k4MHJGZy4MPRGUNN3/JBU5oPidXOYg5TA5J2Q70199A/aVXfKj2G3HBfWFlyhMYZmOJZXmle62WGahOwrJkDX81AX94nkIQL8oN7sVu5sZ1/Ulyc8DHAS87kAXb06HLa0aCpv8mUvf/Mb5pdViu2USEwBpApFgWyX+hJM1ITg9DjCwEulTjJLZ8NF9mF5m9AuUpvCdyR5EQ==</SignatureValue>
<KeyInfo>
<X509Data>
<X509Certificate>PviVc0eVh83NPjtrXd+0vgi2AegIdWE7RDbUFhoN+B9D1l7NyEABzKr5emp2Gzcxqzgt/l9IYkiOnG+ZMbNu7eTwdI8aAHZpO+CNRicuvpNnfxaY+yP7Y/sGb4R35pM3XAsGVmFT8N6KRvRi5SIQmbH9QK5JUFNacTlPrbrwI6/3jVMjnKI3sYxyerimcnGnj89MW8cG+GV72mEJvA1SiQeA8Y572rpcoJwhGuJYJRFbFl5eJRm5l7UVNmkhDU6mTs7rKrsh03zmUUwumNqanir9QPOOa0gjx/6ibeNcxFrPlgqfB08OHN+QIDAQABo4IB/DCCAfgwHwYDVR0jBBgwFoAUmvMr2s+tT7YvuypISCoStxtCwSQwHQYDVR0OBBYEFITg2hZlQ5d8n0k96fdERsEvyUX3MA4GA1UdDwEB/wQEAwIFoDAMBgNVHRMBAf8EAjAAMB0GA1UdJQQWMBQGCCsGAQUFBwMBBggrBgEFBQcDAjBQBgNVHSAESTBHMDsGDCsGAQQBsjEBAgEDBDArMCkGCCsGAQUFBwIBFh1odHRwczovL3NlY3VyZS5jb21vZG8uY29tL0NQUzAIBgZngQwBAgIwWgYDVR0fBFMwUTBPoE2gS4ZJaHR0cDovL2NybC5jb21vZG9jYS5jb20vQ09NT0RPUlNBT3JnYW5pemF0aW9uVmFsaWRhdGlvblNlY3VyZVNlcnZlckNBLmNybDCBiwYIKwYBBQUHAQEEfzB9MFUGCCsGAQUFBzAChklodHRwOi8vY3J0LmNvbW9kb2NhLmNvbS9DT01PRE9SU0FPcmdhbml6YXRpb25WYWxpZGF0aW9uU2VjdXJlU2VydmVyQ0EuY3J0MCQGCCsGAQUFBzABhhhodHRwOi8vb2NzcC5jb21vZG9jYS5jb20wPQYDVR0RBDYwNIIWb3dzZGV2c3NvLmluZmluaXR5LmNvbYIad3d3Lm93c2RldnNzby5pbmZpbml0eS5jb20wDQYJKoZIhvcNAQELBQADggEBAEUDdVau5qJHdcs8nx5+A8ZG2xgVX61ejd6wqqcDyPBIMybxJkoADyvqNvG5Rc2eJBrJGSKP2HK3U4wh6CqW9STXVriPB97MJ8+SbTH/CdSNQKPmYeSDi5vTiiM+f+J1bygCOZRzmdFZs9+bzTJuPHU2Ikh+MWi8muT+XVzvlZkQg0BqxY8ERI5gfolFUBTcpttlv7yuTLYCLTN47JCL7699WIr6uL92j+Pm2nSH6BGAHvKL5O+76s24ScN6/vWO8FOJvV8jEFyKtLYoUudiMuKyjvf4ZQbnIvreMs064FidIx2+JRGRc5aycy4awzTkoLFOt8NDsqoUN5wi6GQ82Jc=</X509Certificate>
</X509Data>
</KeyInfo>
</Signature>
<samlp:Status>
<samlp:StatusCode Value="urn:oasis:names:tc:SAML:2.0:status:Success"/>
</samlp:Status>
<saml:Assertion ID="_c1fc7fb0-df73-445b-b34b-74cd4e3add15" IssueInstant="2021-06-15T07:21:38.991Z" Version="2.0"
xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion">
<saml:Issuer>IssuerID</saml:Issuer>
<saml:Subject>
<saml:NameID Format="urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified">124844464</saml:NameID>
<saml:SubjectConfirmation Method="urn:oasis:names:tc:SAML:2.0:cm:bearer">
<saml:SubjectConfirmationData NotOnOrAfter="2021-06-15T07:24:38.991Z" Recipient="https://rmbeta.morningstar.com/dataintegration/entrypoint.aspx"/>
</saml:SubjectConfirmation>
</saml:Subject>
<saml:Conditions NotBefore="2021-06-15T07:18:38.991Z" NotOnOrAfter="2021-06-15T07:24:38.991Z">
<saml:AudienceRestriction>
<saml:Audience>QA:Morningstar:SAML20</saml:Audience>
</saml:AudienceRestriction>
</saml:Conditions>
<saml:AuthnStatement AuthnInstant="2021-06-15T07:21:38.991Z" SessionIndex="_c1fc7fb0-df73-445b-b34b-74cd4e3add15">
<saml:AuthnContext>
<saml:AuthnContextClassRef>urn:oasis:names:tc:SAML:2.0:ac:classes:unspecified</saml:AuthnContextClassRef>
</saml:AuthnContext>
</saml:AuthnStatement>
<saml:AttributeStatement>
<saml:Attribute Name="payload">
<saml:AttributeValue xmlns:xs="http://www.w3.org/2001/XMLSchema"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:type="xs:string"><RTParticipantInput xmlns="http://www.morningstar.com/retirement" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" TimeStamp="2021-06-15T02:21:25-06:00" ReturnCode="0">
<ParticipantData ClientID="ClientID">
<ParticipantInfo>
<Participant UserID="124844464" FirstName="NAME" LastName="124844464" DOB="1975-01-15" Email="ASPScrambledEmail@sungardebs.com">
<Addr>
<Address1>124844464
ADDRESS</Address1>
<Address2/>
<Address3/>
<City>ARLINGTON</City>
<State>TX</State>
<Zip>760136517</Zip>
<Country>USA</Country>
</Addr>
</Participant>
</ParticipantInfo>
<ParticipantPlanData>
<Salary Amount="76000.06" />
<InstAcct PlanID="123456" PlanType="401K" TPAID="Aaaaaa" Status="Active" AutoEnroll="false" CombLimit="100.0" CombLimitPreTaxRoth="100.0" EnableFutureElections="true" EnableContributionChanges="true" EnableRebalance="true">
<AccountBalance>
<Port>
<Security TransactionID="14" Balance="0.00" PreTaxPerc="0.00" RothPerc="0.00" PostTaxPerc="0.00" FutContriPerc="0.0" CurMin="0.00" CurMax="13429.02" FutMax="100">
<Cusip>759522105</Cusip>
</Security>
<Security TransactionID="15" Balance="0.00" PreTaxPerc="0.00" RothPerc="0.00" PostTaxPerc="0.00" FutContriPerc="0.0" CurMin="0.00" CurMax="13429.02" FutMax="100">
<Ticker>VFIUX</Ticker>
<Cusip>922031828</Cusip>
</Security>
</Port>
</AccountBalance>
<BrkgBalance>
<OverallBalance>0.00</OverallBalance>
</BrkgBalance>
<RothContri>
<PreTaxDefault>
<Default EnableSMART="true">
<MinContri/>
<MaxContri>
<Rate>100.0</Rate>
</MaxContri>
<CurContri/>
<SMART Threshold="0.0" Contri="0.0" Contriinc="1.0" MaxLimit="100.0"/>
</Default>
</PreTaxDefault>
<RothDefault>
<Default>
<MinContri/>
<MaxContri>
<Rate>100.0</Rate>
</MaxContri>
<CurContri/>
</Default>
</RothDefault>
</RothContri>
</InstAcct>
</ParticipantPlanData>
</ParticipantData>
</RTParticipantInput></saml:AttributeValue>
</saml:Attribute>
</saml:AttributeStatement>
<saml:Attribute Name="backURL" NameFormat="http://www.morningstar.com">
<saml:AttributeValue xsi:type="xs:string">[REPLACE:CLIENT_VALUE]</saml:AttributeValue>
</saml:Attribute>
</saml:Assertion>
</samlp:Response>
Example 2: SAML xml
<saml2p:Response xmlns:saml2p="urn:oasis:names:tc:SAML:2.0:protocol" Destination="https://rmbeta.morningstar.com/dataintegration/entrypoint.aspx" ID="_eb75715efaef3d6d32470fd1cf89e28f" IssueInstant="2020-07-07T20:19:57.267Z" Version="2.0">
<saml2p:Status>
<saml2p:StatusCode Value="urn:oasis:names:tc:SAML:2.0:status:Success" />
</saml2p:Status>
<saml:Assertion ID="Assertion-uuid85c2985b-013b-15f8-a84f-816b58513fe7" IssueInstant="2012-12-10T17:00:20Z" Version="2.0"
xmlns:ds="http://www.w3.org/2000/09/xmldsig#"
xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion"
xmlns:xs="http://www.w3.org/2001/XMLSchema"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance">
<saml:Issuer Format="urn:oasis:names:tc:SAML:2.0:nameid-format:entity">IssuerID</saml:Issuer>
<ds:Signature Id="uuid85c29865-013b-1766-8680-816b58513fe7" xmlns:ds="http://www.w3.org/2000/09/xmldsig#">
<ds:SignedInfo>
<ds:CanonicalizationMethod Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#"/>
<ds:SignatureMethod Algorithm="http://www.w3.org/2000/09/xmldsig#rsa-sha1"/>
<ds:Reference URI="#Assertion-uuid85c2985b-013b-15f8-a84f-816b58513fe7">
<ds:Transforms>
<ds:Transform Algorithm="http://www.w3.org/2000/09/xmldsig#enveloped-signature"/>
<ds:Transform Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#">
<xc14n:InclusiveNamespaces PrefixList="" xmlns:xc14n="http://www.w3.org/2001/10/xml-exc-c14n#"/>
</ds:Transform>
</ds:Transforms>
<ds:DigestMethod Algorithm="http://www.w3.org/2000/09/xmldsig#sha1"/>
<ds:DigestValue>7Q1Ofpfq5nIItis08/AyXOdOukg=</ds:DigestValue>
</ds:Reference>
</ds:SignedInfo>
<ds:SignatureValue>P1aJzJ05DqmwX9O8KAp80l4ALN2IQFki1djxI4hJZuY2HL7yBanf7RnbnNBcfL8YymnnlTo+6sQa6gSvagY44hOin1O7DkoP/lBCLKx35YpoqiQWMxDaqKjN7+asAlmWbxv1AvbpaB9t5LSmYPtUAYoQ7JVQ+fvrZ70TwW9cuPY=</ds:SignatureValue>
<ds:KeyInfo>
<ds:X509Data>
<ds:X509Certificate>[REPLACE:CLIENT_CERT]</ds:X509Certificate>
</ds:X509Data>
</ds:KeyInfo>
</ds:Signature>
<saml:Subject>
<saml:NameID Format="urn:oasis:names:tc:SAML:1.0:unspecified">20027951</saml:NameID>
<saml:SubjectConfirmation Method="urn:oasis:names:tc:SAML:2.0:cm:bearer">
<saml:SubjectConfirmationData NotOnOrAfter="2012-12-10T17:01:20Z" Recipient="https://rmbeta.morningstar.com/dataintegration/entrypoint.aspx"/>
</saml:SubjectConfirmation>
</saml:Subject>
<saml:Conditions NotBefore="2012-12-10T16:59:20Z" NotOnOrAfter="2012-12-10T17:01:20Z">
<saml:AudienceRestriction>
<saml:Audience>QA:Morningstar:SAML20</saml:Audience>
</saml:AudienceRestriction>
</saml:Conditions>
<saml:AuthnStatement AuthnInstant="2012-12-10T17:00:20Z" SessionIndex="uuid855d8836-013b-1995-82b9-816b58513fe7" SessionNotOnOrAfter="2012-12-10T18:00:19Z">
<saml:AuthnContext>
<saml:AuthnContextClassRef>urn:oasis:names:tc:SAML:2.0:ac:classes:Password</saml:AuthnContextClassRef>
</saml:AuthnContext>
</saml:AuthnStatement>
<saml:AttributeStatement>
<saml:Attribute Name="payLoad" NameFormat="http://www.morningstar.com">
<saml:AttributeValue xsi:type="xs:string">[REPLACE:CLIENT_VALUE]</saml:AttributeValue>
</saml:Attribute>
<saml:Attribute Name="backURL" NameFormat="http://www.morningstar.com">
<saml:AttributeValue xsi:type="xs:string">[REPLACE:CLIENT_VALUE]</saml:AttributeValue>
</saml:Attribute>
<saml:Attribute Name="sessionURL" NameFormat="http://www.morningstar.com">
<saml:AttributeValue xsi:type="xs:string">[REPLACE:CLIENT_VALUE]</saml:AttributeValue>
</saml:Attribute>
</saml:AttributeStatement>
</saml:Assertion>
</saml2p:Response>
Example 3: Encrypted SAML xml
<samlp:Response xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion" ID="_e36ad9f4-8af3-4e31-97e7-6837c0b7b97a" Version="2.0" IssueInstant="2022-10-05T17:35:43.2429548Z" Destination="https://rmbeta.morningstar.com/dataintegration/entrypoint.aspx" xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol">
<saml:Issuer>test</saml:Issuer>
<Signature xmlns="http://www.w3.org/2000/09/xmldsig#">
<SignedInfo>
<CanonicalizationMethod Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#"/>
<SignatureMethod Algorithm="http://www.w3.org/2001/04/xmldsig-more#rsa-sha256"/>
<Reference URI="#_e36ad9f4-8af3-4e31-97e7-6837c0b7b97a">
<Transforms>
<Transform Algorithm="http://www.w3.org/2000/09/xmldsig#enveloped-signature"/>
<Transform Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#"/>
</Transforms>
<DigestMethod Algorithm="http://www.w3.org/2001/04/xmlenc#sha256"/>
<DigestValue>Wgo4LwL4e/h8zhXPevEqa7m/np6eP2WSOaAYHQyx6BY=</DigestValue>
</Reference>
</SignedInfo>
<SignatureValue>ODuJ2fC9+5S7OBjJgMfeTq1GS3/xMaf1sSSHOtcHLwj34AkcJPs86Y3pD8oXJLQQFYTe9UhrfBfktOoAnHIQWHaLiM3iKG/Uv3XwhvW4Jc/1QRuAa5pyb84JHe4vqzi+C1KGMZZu8U3XPQNP9HpkWxtQpRTa6Fhai0w52CABdqHjCi3LbatmBUxmvqCBAw0dmdobYAOhonZBuxytqQotpqzcwvwWXaNHasPw2bHfT9TdZyjylagvFchrBGWJkr1NyQL3D5MP8QO/lyfvixT8gZE4SrYhOn7mTl5tUWeVALhedZPhFEnJx0pMbCoOCHOJg/olaH5MygTJtpzxZFgfGat9vUhV3zdHvfBw2sfuGjN9skY2IrA+09/wUIVRDASAkd67TQpzEi+t3Ke7a1VNmS4SOT2sQa2Nwy9Cqw7Gk8qhRg05YZYLPMlDFoWyvUYlNp7Qxo95BfoMcqZtd9/UzlN5msI4GzV6M0/5aDJBQSD4p7tyfeeDL8EM5CqKpvJfHIAJb2BFn0HaonAuEyyQNYbgey9z/jf3VGxrIyRk2BcJOibpRJ/CzniMugXrME7JsTOGGPqRtZ5zOJ+CkqfM88vUsW/gqWcGd9VvDOiM79VQzqrfNmrYpW2bUFzVx9K07JAujxP4+0jO5Dpw5iJCOVd8B0hLbmQ6JozrmhlScXo=</SignatureValue>
<KeyInfo>
<X509Data>
<X509Certificate>MIIFojCCA4oCCQCyZNGG5vWH6jANBgkqhkiG9w0BAQsFADCBkjELMAkGA1UEBhMCVVMxEzARBgNVBAgMCk5ldyBKZXJzZXkxFTATBgNVBAcMDEZsb3JoYW0gUGFyazEMMAoGA1UECgwDQURQMQwwCgYDVQQLDANTQlMxFzAVBgNVBAMMDmRldi5ycy5hZHAuY29tMSIwIAYJKoZIhvcNAQkBFhN0ZXN0QGRldi5ycy5hZHAuY29tMB4XDTIyMDkzMDEzNDgyNVoXDTIzMDkzMDEzNDgyNVowgZIxCzAJBgNVBAYTAlVTMRMwEQYDVQQIDApOZXcgSmVyc2V5MRUwEwYDVQQHDAxGbG9yaGFtIFBhcmsxDDAKBgNVBAoMA0FEUDEMMAoGA1UECwwDU0JTMRcwFQYDVQQDDA5kZXYucnMuYWRwLmNvbTEiMCAGCSqGSIb3DQEJARYTdGVzdEBkZXYucnMuYWRwLmNvbTCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBANSeyGwf7RfDbkXfNI5cckgIiCuVz7NA43I5JM5cWMMTJrpvHqQZqmC05RQPrJVlOihs/IfxRHTWyD6H5IB5O/3hxXJJNooBITsMzk/irJZLr8w3y4PXOqY198jtzT1IEE/P9xm7N1E1+VeRBl4KcqTsfztyrjbDZ26ZooVZOsBk1ja13tfhjyTb2+oSCJC+BPuUwnlNbACLSYqf2UN4DfLKSH63cudAzpX8gMK4C7+epxKSh33PCdPpy6o9izej+q+TeNOMoJclFne7q/RwxXWb5AM2YmF7XDiAe8ky+0kzorQj+H066WxQByPySNXPp0N74pW8PcwiYmBn7TSHNYaOi4VTqEnoAh8S4xujaOn93ZSoRLevgOiGCpnPq3Jxn5fvnwV+NCtC4YVrx7RvDwvXZdqHFW0JWvjtpIM4AJdLuCa9K09vUS23iNELrMTcsw03sL6LyHzI18xgdjBWV4V4R0NXCbGHya5X/YZpc1JC+pWUX4RoCMR6Z7stS+Qk+61mO0VDzfUVMZxMTn19hT4ku4h3S0eqh1jS9YoLnfhOmBmt6OV9DCP/u6iyZRLjGBw32nNPJSwjKGkRfaJo1zcN8HzO7+CDZxqwhxt7g95GU2KBLI5NDNYMKHcfI0sxWXtaGsp7i6nkDrFYpd8a/JI9QScocigpjzCSP8s5JtfNAgMBAAEwDQYJKoZIhvcNAQELBQADggIBAAqBnjgAyW34/UQr+yHZZ8D4zdy4/CP/IAjpaS1+fuUNETPztc7viXmwdets9RfQH563y2FziYipsEOjPNpo5nAwWTZjiyyYUeysHqnKH+4eTsSI55N8rcM+KL1CmrRXtpu8mJnhgxRWoqJFp2ukX9uqDOB9xUEEGpKnWEcsGO1w+efPbNapNhfwTycfaPOoHAlmoOJGJC2+fTkOV0yU3at7feJo1FsLhW7eYbEqgk8UqN0At/cxUpEVYYn4pY+TOZX9n0A0lw4MGK8fOhcBxUZH9lBA4GmR/t1WOc5Q5zLBJSkgwMz5djYrlCvM9uVCl+EBcHghr9VdmWrJJedQCxsvHjKCsbLZt2Q32zCN6PSgcuwQwzKbRSWLTKDjCA/dkDTPb2EileuePyS/FKLCKCkaRuRKn6lrq87HmFuSIVAnXkuwtiuqBt+Qf0Y9K2T5L9YJk7ZPrv3bGSQ2V7whkppu1fvYAe8QnJp0Vwp0XYDPIXI2GusJkuN9MFAYnrQjtps6sEstrrI9v1wxIVQCwWUD11H51hmsN+u3eNqCLnF/JIGzZyxItaaoj8fmaI7wbIKskikSQNaYBdX4/Of4viJhezJXYZt8/gC7Bhf9iKaEuRsSODVw4eeruegt+m1Xy8Y5WhCd72NI06IKjJVZn4sDfy4+uzMkZGWGJY0NWOHU</X509Certificate>
</X509Data>
</KeyInfo>
</Signature>
<samlp:Status>
<samlp:StatusCode Value="urn:oasis:names:tc:SAML:2.0:status:Success"/>
</samlp:Status>
<saml:EncryptedAssertion>
<EncryptedData Type="http://www.w3.org/2001/04/xmlenc#Element" xmlns="http://www.w3.org/2001/04/xmlenc#">
<EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#aes256-cbc"/>
<KeyInfo xmlns="http://www.w3.org/2000/09/xmldsig#">
<EncryptedKey xmlns="http://www.w3.org/2001/04/xmlenc#">
<EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#rsa-1_5"/>
<KeyInfo xmlns="http://www.w3.org/2000/09/xmldsig#">
<X509Data>
<X509Certificate>MIIGcTCCBVmgAwIBAgIQD1s+ph0YlNkHS881utZIXzANBgkqhkiG9w0BAQsFADBeMQswCQYDVQQGEwJVUzEVMBMGA1UEChMMRGlnaUNlcnQgSW5jMRkwFwYDVQQLExB3d3cuZGlnaWNlcnQuY29tMR0wGwYDVQQDExRUaGF3dGUgVExTIFJTQSBDQSBHMTAeFw0yMjA0MDcwMDAwMDBaFw0yMzA0MDcyMzU5NTlaMHIxCzAJBgNVBAYTAlVTMREwDwYDVQQIEwhJbGxpbm9pczEQMA4GA1UEBxMHQ2hpY2FnbzEZMBcGA1UEChMQTW9ybmluZ3N0YXIgSW5jLjEjMCEGA1UEAxMacm0td3MtYmV0YS5tb3JuaW5nc3Rhci5jb20wggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQCmoGb7DhiKETVAycQHfAJfnhwmw4bokfpgZGSjztR7d3DbE301byHqdWa3XaKi9uzaS9n8cEY5DhLfc0cXioMjZ0WQLOc7vKcyHIWMtJOiTnuyKa+fVA/tt4spRFjSxE2t3ZaKjqyFYcz+Zi3ciLEU25BeZm2dVSOB+b0/7KGsAEbiLvpyDsFh2s9FO/g2rY0MLVJjIPH9lGzgMxS98uqYSIv464KxD0uNyIz7WF8WR1YpVf5q7zqPuC3PMLlQagbXsQdP+Pe72+Bx/x6mblf5XXJSBLvCcGjdDK667R7+C9x1WHzoeRAh/GfWVXe9XFh/2+qSyI9HgytnXTN/4R8pAgMBAAGjggMVMIIDETAfBgNVHSMEGDAWgBSljP4yzOsPLNQZxgi4ACSIXcPFtzAdBgNVHQ4EFgQUyTsSYitTLMqV7dqoofEdu3y6y1QwJQYDVR0RBB4wHIIacm0td3MtYmV0YS5tb3JuaW5nc3Rhci5jb20wDgYDVR0PAQH/BAQDAgWgMB0GA1UdJQQWMBQGCCsGAQUFBwMBBggrBgEFBQcDAjA7BgNVHR8ENDAyMDCgLqAshipodHRwOi8vY2RwLnRoYXd0ZS5jb20vVGhhd3RlVExTUlNBQ0FHMS5jcmwwPgYDVR0gBDcwNTAzBgZngQwBAgIwKTAnBggrBgEFBQcCARYbaHR0cDovL3d3dy5kaWdpY2VydC5jb20vQ1BTMHAGCCsGAQUFBwEBBGQwYjAkBggrBgEFBQcwAYYYaHR0cDovL3N0YXR1cy50aGF3dGUuY29tMDoGCCsGAQUFBzAChi5odHRwOi8vY2FjZXJ0cy50aGF3dGUuY29tL1RoYXd0ZVRMU1JTQUNBRzEuY3J0MAkGA1UdEwQCMAAwggF9BgorBgEEAdZ5AgQCBIIBbQSCAWkBZwB1AK33vvp8/xDIi509nB4+GGq0Zyldz7EMJMqFhjTr3IKKAAABgAQQEhgAAAQDAEYwRAIgKgoQ2MAiBdmQiYqr/GTJe6T9JplWlF9I1Lmmsjbk7iACIDdgY50o98QzftTEUksm0KNM+TWqE/N6q/a4bjIxPoo9AHYANc8ZG7+xbFe/D61MbULLu7YnICZR6j/hKu+oA8M71kwAAAGABBASAAAABAMARzBFAiBTgzEbKcdgHfDKn4gao6vq5843Aj0QdufQ+3dKq6PbEQIhAPSutH7+dsZgS0fELozd5dIiR2wd7QQyKxikXIvzTySkAHYAs3N3B+GEUPhjhtYFqdwRCUp5LbFnDAuH3PADDnk2pZoAAAGABBASMAAABAMARzBFAiBarsPoNUJUGO3d5a0JAzaU4VlCARLQuLZ5ClsstI0edAIhANWkoMQbJeWeUnbPHCSH3/8S7zwXjKExf2ZhrF/4rfs0MA0GCSqGSIb3DQEBCwUAA4IBAQCTU+NTxIfreDpgd/rdRMGIMbKarKx/AeSAKMskC15MwzW5XtHkSC0i2m2JOxkBN84sSX0ChfCrK3XjTVPX11hbyTRLzevgf0VBRrQ7XzCJsCB3M/8xCBQSkI8XGQ0lhWFcsYPHCYR3jUH7I+9xM74p1gMTav3tHNiFbpQJffX2uvkDUtaZQ825WX8MhZoxBQHrpC+DHWVZEYfapsemPE0+L9ZuEUNiuHfigmbmv+DhWxvrYV72tHcx63cqLdvFPmTuQghZKOtOzZ7tGpkub5NAe2PXhXu65BG50MAeJur5S6LqNghcDWo9ywKW3AENz9B8IA309ELNZ11+nZT7ZwDK</X509Certificate>
</X509Data>
</KeyInfo>
<CipherData>
<CipherValue>T9NJThFBMD9vfxMH/ch01TtAHGVuGeM3OyTObiwisMtqXx7o+zAIDAVem748OkedBMplwWI3alarsjZF67ClOQAbJhV3P/kjXGPaT1sodpnyAg7mODi2rz3dqNMupjfBVje7Bm2KSbt3FADhQDinQzY+yGeifBmQpAQwPFlgMq0PG9ykkoEWp0657NzPG/RnX8DxR5gn12ve6aB/f6TQPOVSXiQgpNlMS2bYvqA0yZYYLS94ogZuTnC5+brVMTlBo8bOfcsS9eDpc7CfLjERqtrv+PXdg+AZAkeTqPhF8BnoQrS5aOU+F+/+bg5h0O5Jy7TxbwowhuQ79cCw0dZvZw==</CipherValue>
</CipherData>
</EncryptedKey>
</KeyInfo>
<CipherData>
<CipherValue>ITws2AOoNnddAJxgcdsExi6Ww8q/M/ASLVsPisKr9dmQs75YZaoSuGycpiFwQLhr9m2bVk/WRn8n0l534m8pcLEOZLsZQvhV/OYVORFO8PKoMtuRAJ/CK64CewvJHCZaunI13J4WqWXV89R7bqsqWn769me8h/ZSfYKEXNLJCA/GFOvwPujHpp1zs0gN4IPoPTE7eb1Abn2jL/GZoIuZdZD03U52WKg65uXqJi+T3kvyy99csA3W1oAYveLsPKPbpUVrEBDdZL2phs+XKk31gRbHvle/lEnw4aLrRjXz7WWOGOD3U+iO3hS2yFJ2P4Ma5/g1tV3efZ9V5aTuX8T0m6ldRLB66Foh85IqBsCXPfkXDEfBrA8Ds4V9un9q3/gDiKLdbm9bssHPszhim7o+oybCLcuH3+aDQxKKJuwaZ2ghjKDJ70hRCLHFA1Mw7UCfy9YLXIwuHAgWbVVHIbLN0RKhbRfAtdM7js2POc4Qyzd7JpK+q82peKUjQktVcdt3JZta7wNgqBS6e+jsdZmVF2N47ROFXEZViNg18jBH47Mlj1SduGrStHwba8w6wkt/FvNkP2S9SFHomRiAdsp3gV6/8CrWb8XiRoOz+DRd3EZAacvVR/0wOXkTwwPAvVv6mfZ6NBiZVWcNnQOu4JZBSPEisoBmJPd1w/uyCeCwOx4A/m8I/WEBq0mlke6fryDMYyyh8Me8HTFBw3YCIsL9AhWtWAlBM/pHnZA9q69rObPhnzkcoPZnIAcPuPnctkjilFS1Uv/b3aNCguabdDUz8bRcK4RviG2kCJr1l/1IN1rhp7bVnD/OzUyTNGL8SSREZewhTbNSxaKeln/poZ+NaFm4QfisnZ9e/6F8+pIEVZseb0rFUoF8uCX33O11uBnezTO5WxE2Yx285hlRdZLON1hAP8xr7/rARMHce08JpKZAulaIwtb8LT8fMWQY4WvBIcYT/9Vf3bguv+ya3d1WxBf8ji0q5XW07ZD6EdDRZTY9IhljRSMAvs2VfxdD1vpUlLWlwfojubVdsL0b5hGcm4/fl2cFC7mLjMOfHwh4VKS9Dv9bHsiN4uHy2JDrAbjTuxrbAa9uV5P5AH6E+q/R3uE+NZeK9leVXz68xfFOpW43K7qTdn4G5OuWNYWPKdvQ0q5dK+vYqspxqRP0tGBWVnpGmfGThvuadZRiJnOOwE76R+dHnKwWPEOXwXE8CUC4k1W5EbcIkU+N3M6S5D2AvXqFgqrrZP4eyvOCezwTjkH/Xq9eWCb8cHK863VfOs0dr8+fDDEL1LTUeGZKgP6PAMpsSY+i05H5S4Zbwhx975mzS8+Uz5CgOnQ1fC8hTTbh+X0eMUWP0i5Qp/2jz8fx35xeTGDcwuGgotj2swZymsCnSTdZXylA/Lgx1CUHfnpwbdBhePXgCpdEufCTkNkVFXue7qJKcZbIzprkdzXdea7IVgBoN3LV9hpVltkPVs1pRBrkNxqdcn1Ig6gmT/ZzXv6eR/AHFBY+0Nk+jgoRcbXB5nNCdHtlYGHnFKf7GSBvUQakJDvhE7md4PrWKZdfZI58zSBatk1Mo1GrTHU9o5xTsvzEajZc77Qox3luRE/VJYvy7pL+AzlZg1JPKpSz1svni3oyRv4KF6HYuxyJWhfVnDWylBoz31ox/E4ws8wI4E8IU78RArcYkFxe5q9sMpEA1c1v3k18TKwmyCN1pqllISzfBmq3YrGwSY+kWNv4gCKjV3wm8U6nJ4LYTntAfoCWICdmcqOoe9vXp2GWoD1ZCQi8fRNy6/Y0aBkji+MIkNppZtq3dtVrOXNxGc6DMrrDhnVwMcf1i3vw0TGsXmISqdQkM3r1s8dBfG9S2okG2CkB6yJwj4Jwij4FhwiU9Tp85jZgAyXD/KHeczed1fb5wsLXHfAMHTBcL5ex6aUVfpRipwCqJffih1TP5bGR8RSwtN5tD9XBFIBnydJfAEkJKNDK7C8IASe/kbsKOFN08LwnemqZfE/SqOqMgwZPhmhJCn9im6oDBHirMCMFvcXMd+85VvNr5VKKi1Mbki2m7Mr3klr3q7V5/dV3I7xVoGq1wTvlHcQ7WbV/bxDUzz/4b6HHA1IGRgn4aR8Yafsse09VUA9r3fEFMMmgPV+w5Lje+zjUL9/HWjctaWP96nUrN4fDQOY/5HbKkq6XfBr5300y2SzbAXznIcdJvKHJXABdNOCemTzYXo1TZnTg5afiNib7Pj1q8Ty+TpMJj2GiVI+yrrSHmAU2SztAGd4lVEXlfVip7AqlJm7T9XdL2KYMSRFIp9Uru1swXS+vYyQkirOMh6gR8oKGjISMkJ6MxVNDLV6u1MaFYOug9Zyc2LCSG3F5p+KpzcmGCE7jp2411N5zkhc6+Yq7uU6Qp9QO3SUVbNvXUbttxYOq9tb//XhRvUta0pPO5JExYhWuUdzzp2IILDJQotFcVhxKI3bWXyZN6vPtpeo/A8GbSzc2zDjLjMWanTGLPBTJWk0CFu3pGWBIwHcspMSbQRZ5RBcoxzAnGilNLB91XIbOjZqwK5eMo/Sbfabm1oT8NKNk6/L1FyXPuHOP/fZ+cva7ZPnZbeEwjylXhjVW2NALujBn7rtsA5lyQb63ACOeb9+P6t26HqgTWB0p5AZONVAJxI4QN/gHI6UkQGV6wMen0NBIVpcbVseczXScY3XH0IEgoquKSB4/KkjuLsJMaFuKH7/sFHCC/kQsV0RkFiA4djlDx78LRDBUwldXfVRRpWgLUUfggPfXl/G+dXA/3K2AyLkDRJbm6KQ7fBIrV4NkTwxKdEUOCt57xY4FJPT09PPms3EtPp4+j25JrIYsq9DDuVehcqKJcBPF+mp53K1+S+6fnsUkvTdemGyIwqh0B/DGCylb+ecTrZjy04HBO/u7iNwhRPbEW7szmbaxomEl4lgWKbEEmEZp+HRK3AzfbjYYkLzBrVjuXYOCVJq65yFs9LD5BNQfau7d8KwA0YqXfdhJMtt233qnA0KhzNMaABWPtNGNIiRAbiDn6cOPlBqvDixws21I3M8JytL9t0fqKzpNF5LQ1f5WA9wIyH1D/8rELIUEsVHF/AyGY00lTKV9k1zNnuFEwhuR7F6vsKgXHy1SDwROkkHetqIeZvUqhKXQFk6Qs1GWJUnEb4IL7QAYt4/mOFtbGS6EJmjyx3+UStS4qN6zN3yuPqZH9c7gsEx/ON3PsLpohZ7frJqcHHQE7V13+bHxMZgJC5HOThML1yl9XkWqnv0+4M7l0Hay6Eq6GH7Hs4wqGZt2QlhWC9k/UW0A1yIHoSWJ42SvtfC6+d215WiXvT2peybcgCvFh5IjVnEujCjLJ1FJbh/SjA2IO5pD2kSx/mdEM2AVx7IifZ0nr3VrKHRC96AE6MJEGDfPa+mHIB78DPBG0kdJM4+AGsNP8RXN9oAcITUxsFsqqWNqpHH5SedrHwhtJWmcm/2n52AtODXHsrRmP4Tcv+quhUyet6em3A+qS9b+heDqFil1jqBdfeGoFjQoj6HECGYSijyo4MX8tJOGcmgUQ29pEak7tt+DTn4FJwOR/2CdKalXbcdAdq+mFcr8xBgVoX0+u5JeZx0qnbnfrpHoiBbXYXA9nEpbM2VahPjK/9jKIlu2h6sML8cdbEIVW0sABfRlJVHmFH7FWydGEArGxvmf8Yn/KUPDEtKWb6DQrnQ/JvSN1qeUWkzgxc3zFzfUcxNRBEuqprl5eN7H3aKcCfDkDDhVqTKwrHaGpZUzACru8E1O5mjBtC5LY/Sw98NyKllakR9PK1r8cUxU9JiiFe1YmwYFFuMKFgg2TXDzk/myvmdsfBjoZUgnI0cQZPuc1ixPJ3N7As96ajfBIu/JYhPl+tiLA7ypSPpYLxhxUmdR/LUCMMC8wNUlY2X62RHAxSKpUOatztisA9YBFJi6KgtBJpp4l3/POs8I6NBEBuQ1sXIl4qA4I0zFsQ/IE2ORNb0nrnvbJ/jeeCUjeT7aOjJJvJ6WBYRSZHONEzOj65ho4V9iWyH+7YHJE81Spa4O6YbdbbjoJCWjN4RYQ2jj/aoyboalWPzBO/k7y0gJTPsTmIm1a/okbvka/gbZFxDH/xiynuYDUEkEE9tUklk0JcAZ8D2IlyTX6du6uwsJnTbFnpPRgeoiWrSx7QDtJJmNpKsHI/fxaNCkoHPCHTQa3V8UnJzkBNhze+0LsXUZpO/2z5Izkpqoc7NqYrEjVvdXbUSGXwDCCTtCKnHo81H29FFfx5PTPJYtf21rAznn7QKbDRViAvv8xycs+JF6Xm5JkRbLjdC7D7wkfFd8VrhyMRPNW1XF6wnVpKX6BKkJKsMwusHKwkra4ZO6Z90JxgEd2O6qCxXc+V9w1Hwzl+yiyqZn1HtsDcnE/aQTVxKy10/w74LbkHCGX+hhFaNfe59u7BquJ3Htobydfn9PXGbFX1OdyT6nP392URpZl2Me1v9azxC68vG5MraJgD6q0ZXMRh052aQaoQg3/yjtskruN9G96969pMZd7re5lBeB450vMAo17hgQYuX5iLSBvDwAoqvoYCUhMzr+RdcCHjwDdwF6a02FJH3KNV+N+VoiyER5RYOaXuZt5JV/fkq6tdIR8YF2VrI7ta74/Uu41zxkD2Z/I7xKnMMhaLWR0Mo6rvzc5mq7y+DgHeE3FsnUFa9MD4Xr8X4SYbRHRe74pRX6uxgt8tNeNk6EwwGUlcsaXI383p1b2qxqKKrLPoFNyiLPv3TXKRj9WeFR4feF1auZRYB3iYeBxtyAh79sUP/A5CKJPHCr6JgDWqGNPWG5UKtkaeEsvEs2IetQ6qj/EiQbZRAvzk8jGArQF+1TJzz83TZKgfXtOhiebDYazPDPs+0OwAdKt1R6sL5o3mUarj9Z8HPigdx8u3Ug23BQxcPB2A3OYaLkGhRU8ALsIRVuOKH2SoiBIE8Crn0wt/tNBL95PwXBndFPebXPfZEy0MXRwbpSZoLYBf9IT58sJlK2twXUbAnp3/DL6AKmM3jfkmX3T6d3KrYu5EWTsiXT+xzrXrK+uS5+5lVqcNiw8y0CbXHmAxv+M/RApq6f0zRhsn+LeZU3s12xBmyAWzmjbd2yuJ7iaydHM7GNCy+N0fuReBwGtf+Br0p8a+oytC8RZRwcJXO22j31lekNilwkEX97ki9uHjmZqugQRC76k4mozH+RP4vY98eOldjo6TEbgCJQXcv7eBo098jsPYt4RerQynt5hGVgviTqlhlZsXdF5IK/pbggwdlVMXKnKY5YYUQgdEjexi6cul5gozJr3X8GdtgUtnnv8vPInVmid/rXLIJLG4PP9lDVTRTswfqk8Y5OQzNYD1hKs5WBAqXu8ETOpwUonCDgN5gbAj8wTw7/GM/IW8ZFSpQBfF7KR7FB7lGBIoBsDWfbPw42C4Rf3Ykv1BScGJaQs72bSkjfNznMdcDopJEJcfkuK61ZtVvM+qsDZCD6OmZhPE9VhxJZyLtW7/5D0w2+5pYgEvJQHbQbpIFLHxgOLvaFWVsoUZrDHv8Cdf5dwsSJKY54uPO0KUcq4Xk/RAwk7kW3UeSsCb4/IO1K7BZYOjQRt/gLviXaV1XhrFgmsBOyzy6Y70Ey5nEhjCysXag9E6qrs9v7X7jVOxayBAZgtvb2tlYB5wQumA53T0pUv6F8AhTy/Vxz6ag/KVgJzGFpy8aISMznjwTlLZfjKlJLFDyx4eMZR6tiD9dCTD/5K/q55V9DqpbzpH8nXWppb7r4LmWpVwV0uqQWwtJP8R1Ub6qmnb7SnXrNHJrstg+o5mQLAEH+/yLWzZ0fOVNaaXTLTmlcAvgbk82X57fQHd8Af/WNpyoehJwsS0YLcIixiTzhFu20tjdeBKc3CJ/SYeuPmVaOp4w3x9LAB7O39qRlVyqFhRFkqWD4RpaErdGYzd99H8DYue0UefvTvp9m1G5nj/IKfuWnog7jPkVF/b8YVDmXZ4zusloSCrTSs/4wJfSd9tLD7g6CZ+yKos34vWBb78eUmnFKzruj7g8XNpfmKxNGuIl0EmUs4UNXRsH8lDEDqdJKP1GriM8dBGyltnbJuZvjubzVja1NPRTQG2zO65Dx8En0wPNzn5vVvDMxEGVRg1fAAoWzGazqDMw3Cqf60kJTp4KRhMsDYDwLnltMQ15MgnUKfvuYqtBAnzGZE9Mw+OtzndccDLnso7L2VRgcgNCFcE8T+xgsuW2cHrMCUGc75SaviPC7LRnR/UzGZkBvnOs7hKfbSmLcoPuTvuesral7TOXI3+JsTLb32orfjnVQsz2SOrhEXkFX02+L6QJchZ14h/9GvILo9DNpaYgowRxb9fdY0Loz1bUGIumAFIOcCeSarcuEuFhfEw3C31zbh6xxUx5gtN+gJBSsbwvaTH9+MHkuSRi3F/LfSUjI14qzgf39WPNIxS7exvAVpNFtbhDV3gNzA4c6l/dJI6Kmr0CgQNfdzrNvnQwfEfoaViMDLoU3wEYx+0w98d4VroJGfs6qq5TTf/ttrpWdeiHdaGml/ghZQJ4NeNIKjWn/iYNvxk3x4nyfEIitgS+QsHmeYDlUJYHbM2bB5oS+ZkqxXYuR+1mV+HvvBGaKvDiKGtrzMaswVgkRNIqUVJiRivT0ACcMuW/QbR9ktsKSv6AP+IVCrBSY/4rZlheJEu1xZI54CsAHwztqqsyQl82vZ608Usnj3lzfwEAAglj9BnNHt7kyqK7xNm4uWuWZaaUPTMsOUSV7wsGiloGxx+Ch2Ysq0Z7kHOjt0hF5I2sjrG3OY2FPD6mmLgiHXPgwZ3yFRChpoLbYoLuNzauHWyPS+4f0kI8bD/RceD9lKWosKIJXbpblZYh2gBJnFp4L46FTO0tq7kiPMMMb0rcOW2NRTVrv7Ub5WTeayb4lw440zipUFUp1N9g+5jWAW51QhL4Gkv2G+PYm5XuLOp0i70gnxnAvNtJ2/drQYyOlEfbg53xi4q0sE86YdCfvB70IgKIta6QZRqzNlJJX3jZpZWUbGad943J9GSLzdkOszeU35JFx6iuTneocXske4S6mg/KA2xjLWnZD2rnYF4wQ6hlkoMUgKDg2Bw0sN8Q2MWzFknqaMrLk/fvUuxyP9CPjlRw8JnSda/8Wr635rCaDxApWGTsB5F4vxuTQbvEJ8qdfuXN4c+x/svZkI3soDoVr+jLgLa1Mbbve1aGBrWnAQuu8EM4ST0CZuL0ARYC0JykWhs+CjpiPlLAtPBbtUlJ1CwtvdZ/9120chHd6omysg25Oh9f7JKgMZOq/JKTVNFN6rQQ2U0bgJXExZXzp+I9GzdFaPUK8TjAEeltVCT/6ecCyaI+Q1txeN9YLWlkwaSr9RKpRRx7sJ6nQhs7FsnKum58xPYoExBABk/N3cJCGx2ES5IsYu+QzfWKkraxswTAKHloTmav0N8rcRs55lgsp8xW7avX8eQIMoD+wt5lPxQJgsTEVZGkeOSect9jiUEh5ps9F0oy8Oc23vwNgIgKSEdG5R5gQ3UaIB9TZT1wycvLc6NJS+qnm4oCkOEFuccJOrOzV+6J/zlA5BUkE2WZDKrXtH7+d1NV+Gv/yQLsoLPxP8XlDoRQ5qnGctJHrWXj9DCYWn21Uw90rO98U96Nkqytm81KCxm0/ltMHwHCNXjKmlWfxAjel2RChY0Jfds0QhQ7YO9aDp71ZaWD82XE29Ub5quzAIJKl4dSOEvslRmFzSzC/9m0jNXl7lAMuVZY2B4TsxPfjhT7ewm3NoGnYlGECZF1gkk/ysR87wH5fIf66F+UZz6ttQbhRsag6j+VYJBjDkV1pN+NER1ihB90aADplNsWiETSyAyGP3Plb9piN6Wm0qjBSyccRzTD2eX0U5Jq7yhjk/FKEnaYhWDyuXGTgRIVLfCTtGaB7Socj4emr5E5UM3OT4UODIWob8IwV6MqeYA5wMdE5e9NOLfD6SZZgi+xbIG1RTz/ce2Z1x5jlmIDqu7pgGXOXidv+hzMv/eKFW+GVhvtqvGGfEn/MbaJPfx39QsB3bNnM1i/K7i6VLrpPsAWdNU1+OVcI6ywLW/ilQHin7+/zvsyz5aubf9fQkWhHSfVYiRmhK5u8e6KvZWwKMs73fjQ55d2iJrKCeEm0EmqQZC8Sv9g0GFWK6mj+VgkAW7f1i4pcO3+URNSsA9MdAaTcc1cPam2J/ZaSofMfpmbP8bCrgVT/Tnvb9cVUs4zBB/WLI9Y4fYg9Hd64uklLiIKM9731J3zHmvj62fB78Myuxpy12Sox3qWRKjdgJbkCP8EwY691dAFC8P/IFFuNWXbYJY+w8KnjKtKj+5WdDlYm5R8mkOI7ZXLil0ME4fxMKJriGyebRFFynuaQl7YZWJXps3Db4I6G70tqAuNFD+oUeut+flSbZCm4KV0NCbt8WDyddG80pncqs6nTr7Zc7eJeJE3gHh3Vw7DbGZf2+4Af1DEAqncYpUEMNM1KvaEVZl6tetYpqUjd0ZxpLnILhnHMoB5YtXzY5iAjpGZGecGCU+fJKqaRly1aGopKxLhBKFieQVx4MU1AEAmtzQv+qt86xmkww9/3PoH5J26q8XALheSFCQstk0rK+Ja0DC+iE9oajFzfdaQretntw0CkSrgbAd9ns/8bP80Ofo15o1/G7t1sLMv/k3Yrm6IQXJ2ZuNBEjfNCeG5gflgcrkmAa6GrcfDms7beMsdID6IM0a8IBLcZf03JxLooElmrUpYDloXWipUThYho6isYoSu/g1/fMotjLiT1XTDrb47iib1F0V1IyARyYxFfMoqTbiAIBYGAQJnjD7Gv44i7GCLkeBPmEbQDwmsxoH7dRZmxKxpBA3B5jCCzTt+28mn/RlYN1kl7lK1TC71YqXHSeDakun1QwpPIlUkKYE7YjIiiodCSQ0t8QBD8G+5+b6F78bGpkVmnd5Dqo3q58cjh3XuWZcrtuCkMVc0WvtdGYQXmfsZ+0OcL9yRUzkqscV231SkKPt9hap+5WanHjMSz03OCct9Pe318Pw0hBWZVhbeQcrhWY1PF1cMMEOzXi5MSlFKU1xjlGI6esQky+c2bPThEUrpi4ZGJ72UzZCxANtck9mcYHGbKsusvP9BOtxv1exhgQMflOaC0khxNGkE3ds+/+9qlEBCanL7wmqNiPlsmJfaJcRV/C11q3GDIMCFP78KH3XuRpDLx8OYEffmKk3wdXs/If45/tLHXGrNqa+Mmy0GJ10jWlodKcHB4/AXBwz0z5oBXjKF1db67WiIXadpNOXuiWKt3JPAN84i77yN9/pKKBbMQQGb2l0aD+gvyCB4o+2uJI91JI5w2hS0Yy+ANSpvcCxNVzFnfe6NU4I7qhYQ7ye59iv3YkPXwCjGmObpYfFYgaZ1ZXG0+GXMDNpBDrTRYUSXltDgw5EE+IUXQCmdgtDNhWwvt6EiZrbDliD3+S9tSKZSzqVncZKpUNGHJo+RHzilyqiL+wpBOG5RLLmOtZ6pUD5vyIFnZ+tdxgZobkYHmwGzVVjYU6Inqw9MjJeLiGpT3qvpIbTkLJ+j9ME34y9YiQu3uOPhkBvyVgExb8N4tR+o0CVtl2uPbzA+qIPhw3F9ub/COW0LfBPOd/4I3WqTgg1i7ZfqOK6hvkX1LXVLRC/ve+hmV18qczJTgtNxtfjoWttdGMyj666D7S2d4EjxVrPM4b0asY6CHxLkBf5rxItpK1uC0RF4g0rCYRkbp/ItOIxEUtKGJmLnKjUdSTxIc1yyi8I3llM4MCc6cVvgrPZwMEIDKI6UUsqKFNkNT9y8VauzulgR3exdsPjlZjevNRNZ6/MhyjNet2IrhH6goJKnWCzbQQKD3DGtox9/pht/oXlBT3LRKAs9GgFlZwtNm3CtR03Hc8SQuJdEoPc8VwB7ZT3cQXpzGGZx7XI/yp5bWyF/M7dKmGC60deQyeoMp908c/iTpcLwZuOsL4y866oeB6oLN3Nxe8abh2FXiLmenUjOIlNKClNywss4MrbemD0y4HdbpPLtuvqioJn08ImMELAWKnXN66agg2OOTzlfmjOw9T5ZKgsLQOm14b/xp8wSdh1cjzvAC3QaWHCwrNk9kV1KDZ0hBn/IAR9WhLUUVMWRQQQaMxZU7sC+IXJr/CgluwW00Kti+ZBnp3Cx/jiDzeXHRsAY+iXbU/OhbS+IBxfAHlKMPHuTlh5EjWi4uiqdDzp2SXPL40/gVLvtt9tcm8p1lLirKUxcn3P18NpsxbeOeraMhTFg5ZlrKuY3bnxtA1iYyKVjFEmI/jzpSQyJLXZ3JXsljAe7I5JTEQ9Wh4ySGwdadStbDTN/PPQWa6wLIMjwllNr3AB2ZV8+8Abl+QrCgybmSp5bjaf/o2aun1N2K3qeZxK/6Vxs=</CipherValue>
</CipherData>
</EncryptedData>
</saml:EncryptedAssertion>
</samlp:Response>
Optional:
- backURL
If a client wants Morningstar to redirect them back to their website in the following cases:
- When participants sign out of Morningstar® Retirement ManagerSM
- When participants click the Exit button after completing session
If not provided, typically the active window or tab will just be closed.
- sessionURL
Morningstar can keep the client website session alive while the participant is in an active Morningstar® Retirement ManagerSM session. This allows the participant to return to the client’s website without needing to log in again after completing a Morningstar session. To provide this functionality, Morningstar® Retirement ManagerSM uses the value sent by the client in the "sessionURL" attributes in the SAML request. Morningstar® Retirement ManagerSM will issue an HTTP GET request to the sessionURL at a set interval. The interval can be specified by the client using the timeout parameter defined below. The default interval is 10 minutes. This will be an Ajax GET request made directly from our front-end. Morningstar® Retirement ManagerSM will ping the sessionURL upon an occurrence of one of the following events:
- When the participant initially comes to our site.
- Whenever the participant loads any page by navigating back and forth within our application.
- When the Extend my Session button is clicked whenever a Session timeout related modal dialog is shown in our application.
- timeout
The timeout parameter should be sent in conjunction with the sessionURL parameter to indicate the timeout value. Morningstar® Retirement ManagerSM will send a ping to the sessionURL It is not required to keep the session alive. If the client timeout parameter is not sent, the timeout value will default to 10 minutes. When the participant accesses Morningstar® Retirement ManagerSM, Morningstar checks the live session time against the client website’s timeout value and calls back to (pings) the client’s website (at the “sessionURL”) at regular intervals to keep the session alive. Morningstar will ping the client website at intervals of two minutes less than the client timeout value sent. For example, if the client timeout parameter is 8 minutes, we will ping the client’s website every 6 minutes. The Morningstar® Retirement ManagerSM session has a timeout value set at 30 minutes of inactivity.
- transactionURL
Morningstar uses the transactionURL value to send the HTTP transaction requests should the participant choose to enroll from Morningstar® Retirement ManagerSM web UI. If the URL is static for all participants, then we can store the static value on our side and this attribute is not required. However, if the transaction URL will be different for each participant (for e.g., URL includes participant Id), then client must send the transaction URL in the attribute during SSO. The URL can contain querystring parameters like “?abc=xyz”. Morningstar will send transaction request to the URL exactly as it is sent including these querystring parameters.
- sessionVerificationToken
If client wants to include an identifier that they want sent back in the transaction request that Morningstar will generate, it can be included as a SAML attribute with name ‘sessionVerificationToken’. If present in the SAML, we will add this value as an HTTP header in the outbound transaction request that Morningstar will send to the client. The HTTP header will be called ‘sessionVerificationToken’ and the value will be the same as sent in the SAML assertion.
SAML values for Production vs Non-production
| Element | Non-production | Production |
|---|---|---|
| saml:Issuer (defined by client) | Value provided by client to Morningstar during development phase | Value provided by client to Morningstar during development phase |
| samlp:Response[@Destination] | https://rmbeta.morningstar.com/dataintegration/entrypoint.aspx | https://rm.morningstar.com/dataintegration/entrypoint.aspx |
| saml:SubjectConfirmation[@Recipient] | https://rmbeta.morningstar.com/dataintegration/entrypoint.aspx | https://rm.morningstar.com/dataintegration/entrypoint.aspx |
| saml:Audience | QA:Morningstar:SAML20 | Morningstar:SAML20 |
| SAML Posting URL | https://rmbeta.morningstar.com/dataintegration/entrypoint.aspx | https://rm.morningstar.com/dataintegration/entrypoint.aspx |
| SAML signing certificates will be different | Provided by client to Morningstar | Provided by client to Morningstar |
| SAML encryption certificates will be different | Certificate provided by Morningstar (Certificate name rm-ws-beta.morningstar.com) | Certificate provided by Morningstar (Certificate name rm-saml.morningstar.com) |
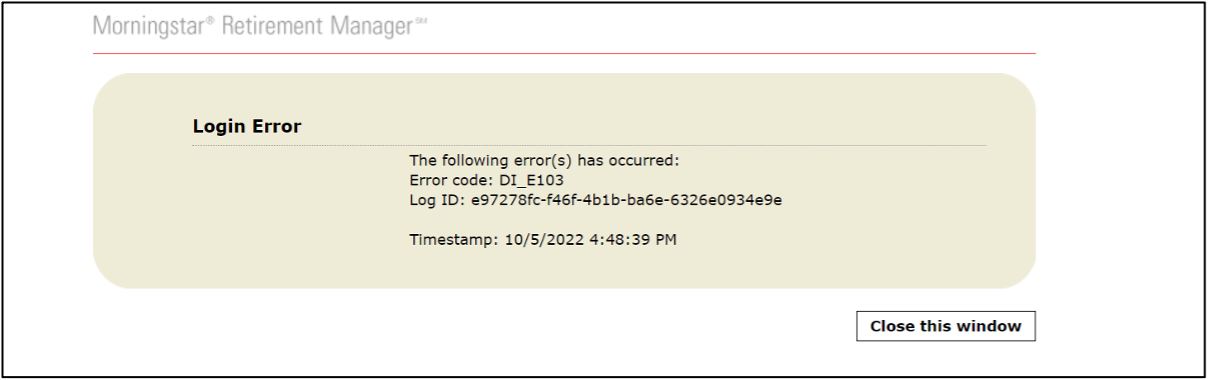
Login and Data Errors
If there is a problem with the seamless login process, a Login Error message will display. The following image is an example of a login error:
SAML FAQ
Q: What are the common errors encountered with SAML assertions? A: The following list contains the common errors:
- Invalid IssuerID – the IssuerID must be provided by client to Morningstar during initial setup. The same value must be used in the SAML Assertion. If a different issuerID is used in the SAML Assertion than the one provided to Morningstar, SSO will fail and an error will be thrown. Please note that an IssuerID needs to be provided to Morningstar for both UAT and Production environments.
- Invalid Audience – The Audience value will be provided by Morningstar to the client. Our Audience value for UAT is “QA:Morningstar:SAML20” and for Production is “Morningstar:SAML20”
- Invalid signing Certificate – The SAML signing certificate must be provided by the Client to Morningstar for both UAT and Production environment during the setup phase. Morningstar will install these certificates in our environments. The SAML assertion for an environment must be signed using the same certificate that was provided Morningstar for that environment, otherwise SSO will fail and an error will be thrown.
- Invalid encryption certificate – All SAML assertions sent to Morningstar must be signed with the signing certificate. Encryption of SAML assertion is optional. If client wishes to encrypt the SAML Assertion, they need to use the encryption certificate provided by Morningstar. Please inform Morningstar team to receive our encryption certificate.
- Production vs Non-Production destination URL’s
- Missing participant XML attribute in SAML – the SAML assertion must contain an attribute called “Payload” that contains a valid participant XML string that conforms to the Participant schema shared with client.
Q: What version of SAML do you support?
A: SAML 2.0 and 1.1
Q: What SAML profile do you support? A: We support IDP Browser Post profile SAML assertions.
Q: Is Encryption mandatory? A: No, encrypting the SAML assertion is optional.
Q: What is the SAML token validity lifetime? A: We prefer the SAML tokens to be valid for at least a minute. This helps us accommodate network latency and server availability related issues and gives us a longer time window to process the assertion if needed.
Q: Which SAML attributes are required? A: Only the Payload attribute is required.
Q: How do clients validate if the SAML assertion is correct? A: Clients can try to SSO into our UAT environment when ready and will see our landing page if everything works well. Otherwise, an error page with a logId will be shown. Please email us the logId and other details including the SAML assertion being tried, the time of testing etc., and we will investigate.
